
Risk actors are abused by hyperlink wrapping providers from respected expertise firms and masks malicious hyperlinks that result in Microsoft 365 phishing pages that accumulate login credentials.
The attacker took benefit of the URL safety features of Cybersecurity Firm Proofpoint and Cloud Communications Agency Intermedia in its June-July marketing campaign.
Some e-mail safety providers embody hyperlink wrapping that rewrites URLs in messages to trusted domains and passes them to scan servers designed to dam malicious locations.
Justification of phishing URLs
CloudFlare’s e-mail safety workforce found that the enemy justified the malicious URL after breaching a certificates level and an intermedia protected e-mail account, and located that it’s seemingly to make use of unauthorized entry to distribute “wash” hyperlinks.
“The attackers abused the proofpoint hyperlink in quite a lot of methods, together with multi-tier redirect abuse utilizing URL shorteners by compromised accounts,” the researchers stated.
“The abuse of Intermedia Hyperlink wrapping we noticed additionally focuses on gaining unauthorized entry to e-mail accounts protected by hyperlink wrapping” – CloudFlare E mail Safety
Risk actors first shortened the malicious hyperlink after which added an obfuscation layer by sending it from a protected account.
Researchers say the attacker lured the sufferer with a false notification of voicemail or shared Microsoft workforce paperwork. On the finish of the redirect chain there was a Microsoft Workplace 365 phishing web page the place I collected my credentials.
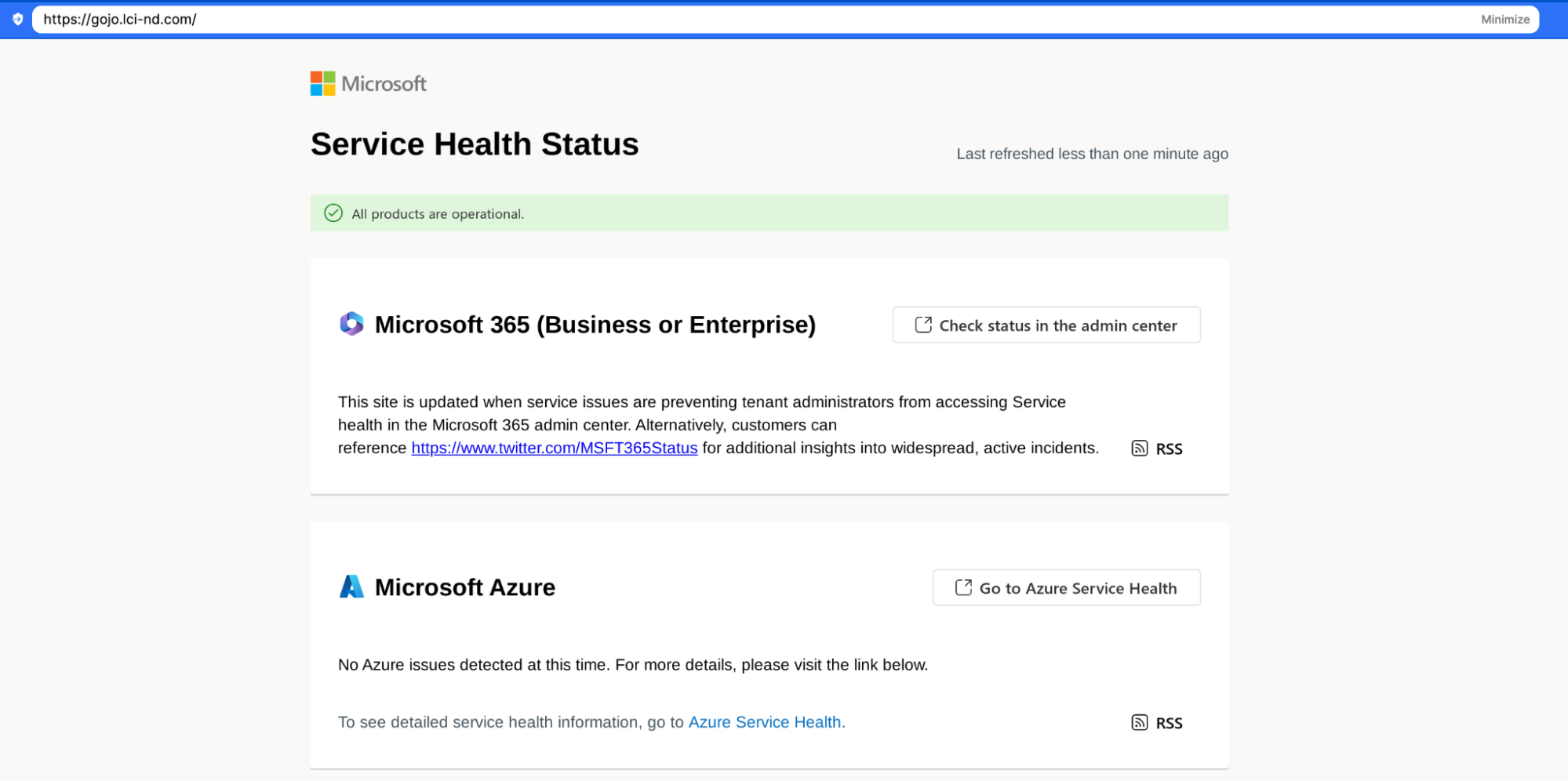
Supply: CloudFlare E mail Safety
In a marketing campaign that abused Intermedia’s providers, menace actors pretended to be “Zix” safe message notifications, delivering emails to view safe paperwork, or impersonating communications from Microsoft groups that notify you of newly obtained messages.
The hyperlinks which can be allegedly related to the doc are URLs wrapped by Intermedia’s providers, redirected to faux pages on digital and e-mail advertising and marketing platforms, and are contacted by Companue Constrent, which hosts the phishing web page.
Once you click on the reply button for faux workforce notifications, a Microsoft phishing web page has been created to gather login credentials.
In response to CloudFlare researchers, menace actors elevated the probabilities of profitable assaults by disguising malicious locations with respectable e-mail safety URLs.
Abusing authorized providers to offer malicious payloads is nothing new, however leveraging safety features that envelop hyperlinks is a latest growth within the phishing scene.


