Scattered spider hackers are actively focusing on virtualized environments by attacking VMware ESXI hypervisors in US corporations within the retail, airline, transportation and insurance coverage sectors.
In accordance with the Google Menace Intelligence Group (GITG), attackers don’t embrace exploits of vulnerabilities, however proceed to make use of the same old tactic of counting on totally carried out social engineering to “bypass mature safety applications.”
Scattered spider assaults
Researchers say the gang will launch an assault by impersonating staff on a name to the IT assist desk. The aim of a menace actor is to influence the agent to alter the worker’s Energetic Listing password to acquire preliminary entry.
This permits scattered spiders to scan community units in IT paperwork that present excessive worth targets, resembling domains, names of VMware vSphere directors, and safety teams that may present administrative privileges in a digital surroundings.
On the similar time, it scans privileged entry administration (PAM) options that may maintain delicate information that helps you migrate to worthwhile community property.
“Armed with the names of sure high-value directors, they make further calls to the assistance desk. This time, they may impersonate a privileged consumer and request a password reset, permitting them to grab management of their privileged accounts” – Google Menace Intelligence Group
The hacker then works to achieve entry to the corporate’s VMware VCenter Server Equipment (VCSA), a digital machine that enables administration of a VMware VSphere surroundings, together with an ESXI hypervisor to handle all digital machines on a bodily server.
This degree of entry lets you allow SSH connections in your ESXI host and reset the basis password. Moreover, they carry out so-called “disk swap” assaults to extract the important NTDS.DIT database in Energetic Listing.
A disk swap assault happens merely when a menace actor powers on from a website controller digital machine (VM), can detoo the digital disk and connects it to a different unsupervised VM that controls it. After copying delicate information (such because the NTDS.DIT file), undo the processes and energy of the area controller machine.
It is very important be aware that by acquiring the extent of management scattering spiders within the digital infrastructure, you’ll be able to handle all out there property, together with backup jobs, snufots, and backup machines that wipe the repository.
Within the remaining section of the assault, the SSH spider leverages to distribute and deploy ransomware binaries to encrypt all VM information detected within the datastore.
Primarily based on observations, researchers at GTIG say that scattered spider assaults have 5 completely different phases, permitting hackers to maneuver from low-level entry to full management of the hypervisor.
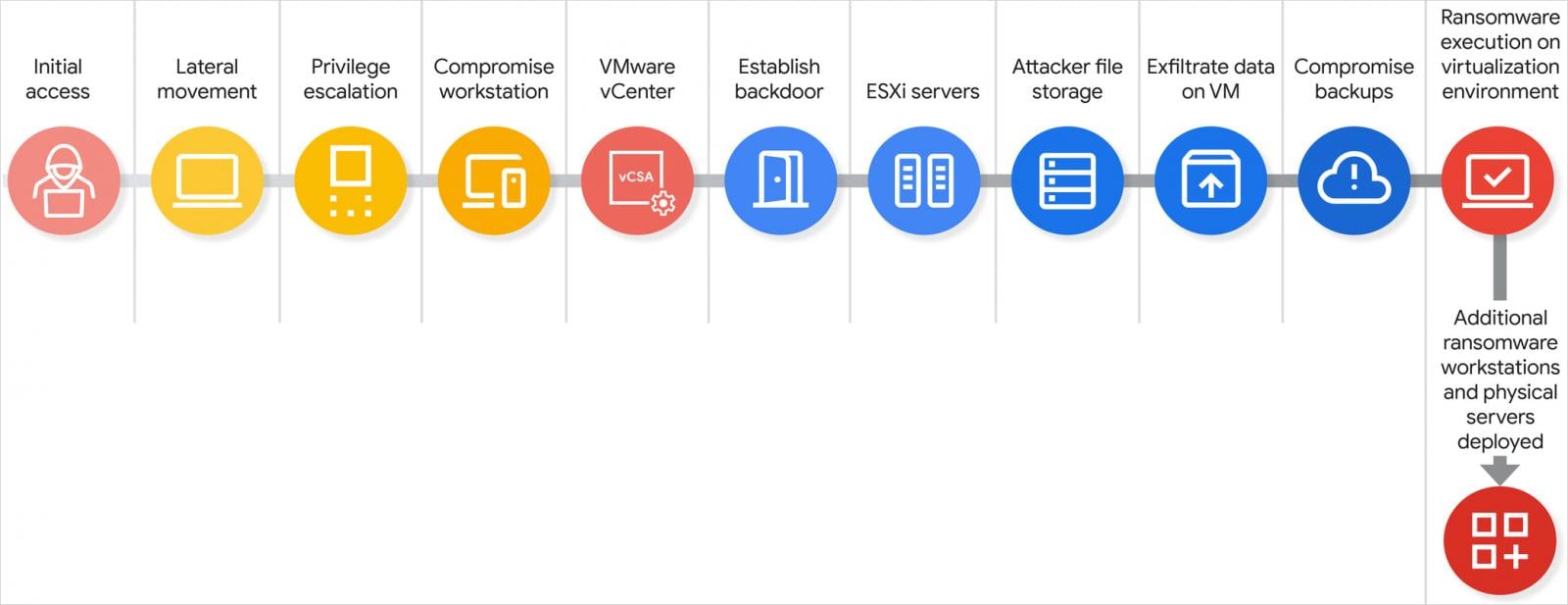
Scattered spider assault chain
Supply: Google
A scattered spider assault chain, totally full from information delamination and preliminary entry to ransomware deployment, can happen in just some hours.
With out exploiting software program vulnerabilities, menace actors “have an unprecedented degree of management over your entire virtualized surroundings and might bypass the safety controls inside many conventional company,” a Google consultant advised BleepingComputer.
Though the focusing on of the ESXI hypervisor is nothing new (seeing the distinguished violations of scattered spiders just like the 2023 MGM Resort Assault), GTIG says it’s ransomware teams which can be hoping to undertake this tactic and improve the issues.
One purpose behind that is that the enemy has realized that VMware infrastructure is just not properly understood by the group, and consequently, it has not been firmly defended.
To assist organizations shield in opposition to these assaults, Google has revealed technical posts that specify the scattered levels of spider assaults, clarify why it’s environment friendly, and supply actions that companies can take to detect violations at earlier levels.
The proposed measures may be mixed into three fundamental pillars.
- execInstalledonly, lock down vSphere with VM encryption and disabled SSH. Adverts might be straight linked to ESXI, eradicating orphaned VMs and avoiding strict MFA and entry insurance policies enforcement. Constantly monitor configuration drift.
- Use phishing-resistant MFA throughout VPNs, ADs, and vCenters. Isolate your Tier 0 property (DCS, Backup, PAM) and keep away from internet hosting them on the identical infrastructure they shield. Think about a separate cloud IDP to interrupt AD dependencies.
- Centralizes siem logging and alerts about key behaviors resembling administration group modifications, vcenter logins, and SSH enablements. It makes use of immutable air gapped backups and makes use of check restoration in opposition to hypervisor layer assaults.
Scattered spiders (often known as UNC3944, Oct Tempest, 0ktapus) are financially motivated menace teams specializing in social engineering, to the purpose of impersonating company staff utilizing acceptable vocabulary and accents.
Lately, it has boosted its exercise with assaults on massive UK retailers, airways, transport and insurance coverage corporations.
The UK’s nationwide legal establishments have arrested 4 suspected members of the group, however malicious actions derived from different clusters haven’t subsided.


