gaming peripheral producer Endgame Gear warns that malware is hidden within the OP1W 4K V2 mouse configuration device hosted on its official web site from June twenty sixth to July ninth, 2025.
The contaminated file was hosted at “endgamegear.com/gaming-mice/op1w-4k-v2”, so customers who downloaded the device from that web page throughout this era had been contaminated.
Endgame Gear is a German PC gaming peripheral recognized for its Promeme Gear, together with XM and OP1 collection mice. It’s extremely regarded by reviewers and aggressive gamers.
Whereas not as massive as manufacturers like Logitech, Razer and Hyperx, it’s a revered entity within the house and one of many main startups within the ultra-light gaming mouse phase.
Final week, the corporate introduced that the “Endgame_gear_op1w_4k_v2_configuration_tool_v1_00.exe” device was compromised by malware with out offering particulars on how the violation was dedicated.
“Now we have discovered that the model of the Endgame Gear OP1W 4K V2 Wi-fi Mouse configuration device that may be downloaded from June twenty sixth to July ninth on the OP1W 4K V2 product web page comprises malware,” reads the announcement.
In line with Endgame Gear, the malware was eliminated and the influence was not affected as the primary obtain web page (endgamegear.com/downloads), Github or Discord offered the clear model.
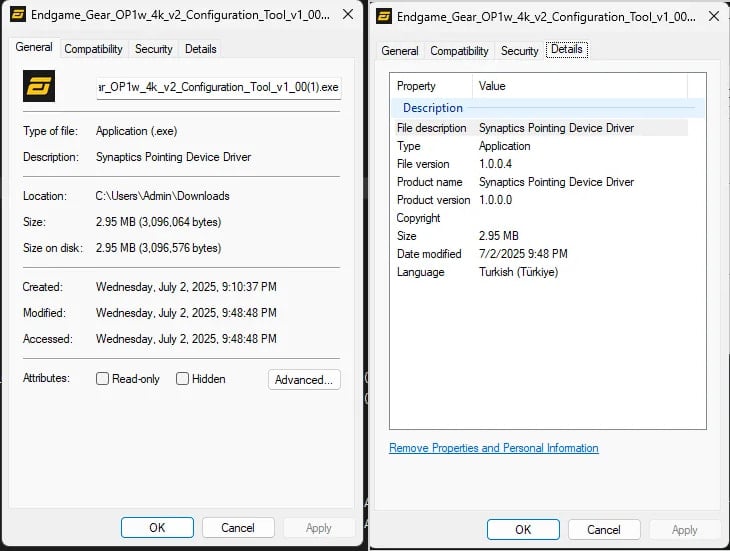
A report on malware about OP1’s configuration instruments surfaced on Reddit virtually two weeks in the past. Customers spotlight some necessary variations that counsel that the seller’s website hosts the Trojanized installer.
The 2 key variations are the inflated measurement of two.8MB (from the clear model of two.3MB) and the “synapse pointing system driver” that seems within the file properties (as an alternative of the reliable “endgame OP1W 4K V2 configuration device”).
Supply: Raccoon597 worthy of reward | reddit
The malware household was recognized as an Xred backdoor for person scans, however Endgame Gear stated it was analyzing the payload and had not confirmed its kind.
Xred was beforehand noticed in February 2024 when cybersecurity firm Esentire impersonated a synaptic pointing system driver. The malware was additionally distributed to Amazon through Trojanized software program geared up with a USB-C hub.
Endgame Gear recommends that anybody who downloaded the Trojanized model of the installer removes every little thing from “C:ProgramDataSynaptics” and redownloads the clear model of the device from this web page.
Malware consists of keylogging performance, permitting distant shell open, information removing, and contaminated customers ought to carry out a full system scan utilizing the newest antivirus to make sure that all malware stays are eliminated.
Moreover, you have to to alter your password on all delicate accounts, together with monetary establishments, electronic mail suppliers, and work accounts.
Now, Endgame Gear will abort particular person obtain pages and add Sha hash verification and digital signatures to all host information to make sure file integrity and writer reliability.



