Microsoft warns that Cyber Espion Group, linked to the Russian Federal Safety Company (FSB), is utilizing native web service suppliers to focus on diplomatic missions in Moscow.
Hacking teams tracked by Microsoft as Secret Blizzard (also called Turla, Waterbug, and andomous Bear) have been noticed to contaminate methods of diplomatic missions with customized Apollozadow malware, using hostile (AITM) positions on the Web Service Supplier (ISP) stage.
To do that, they redirect the targets to the captive portal and trick them out to carry out downloading and working malware payloads disguised as Kaspersky Antivirus updates that set up trusted root certificates.
As soon as deployed, Apolloshadow methods compromised gadgets into figuring out malicious web sites as authorized, permitting menace actors to take care of long-term entry to intelligence gathering after they’ve penetrated into the diplomatic system.
“That is the primary time Microsoft has been in a position to see its potential to espionage at Secret Blizzard’s ISP stage, which means that diplomats are at the next threat of being focused by Secret Blizzard’s AITM place inside these companies utilizing native Russian web suppliers and telecommunications,” Microsoft stated.
“This marketing campaign, which has been ongoing since no less than 2024, poses excessive threat to international embassies working in Moscow, diplomatic teams, and significantly different delicate organizations working in entities that depend on native web suppliers.”
Microsoft first detected the assault in February 2025, however the firm believes the cyberepion marketing campaign has been lively since no less than 2024.
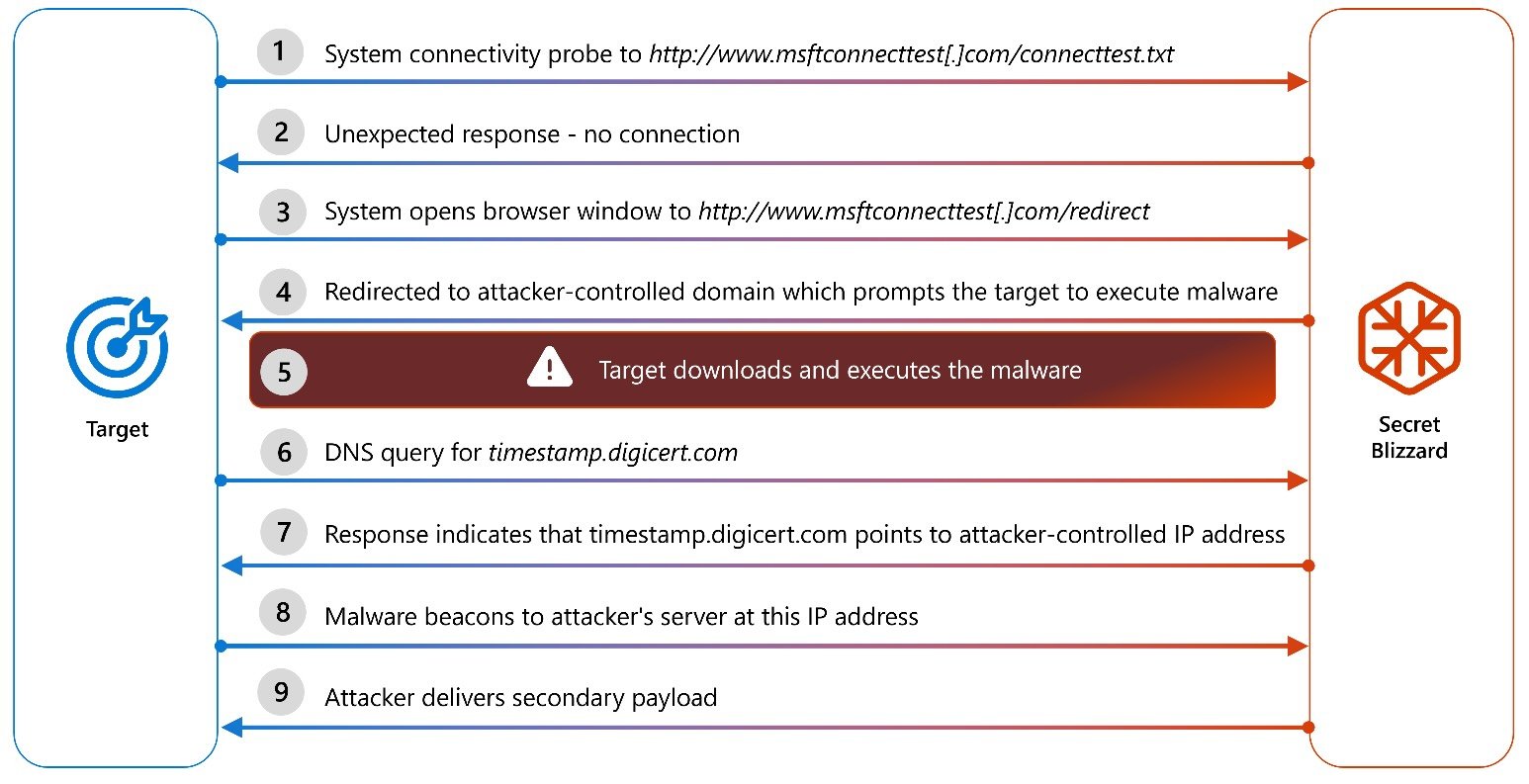
Secret Blizzard An infection Chain (Microsoft)
Secret Blizzard Hackers additionally make the most of Russia’s home interception methods, together with the Operational Analysis Actions System (SORM), to run a large-scale AITM marketing campaign.
Unorthodox Cyberspeas targeted on well-known targets
Turla has coordinated info theft campaigns with cyberespion, concentrating on embassies, governments and analysis services since no less than 1996.
Two years in the past, CISA linked the group to Centre 16 of the Russian Federation Safety Providers (FSB) and linked the peer-to-peer (P2P) community of computer systems contaminated with Snake Cyber Espionware malware.
These Russian state-supporting hackers are additionally the primary suspects behind assaults concentrating on the US Central Commander, NASA, the Pentagon, multi-European ministries of the International Workplace, Finland’s International Ministry, the EU authorities and embassies.
The menace group is understood for its unconventional ways, similar to controlling malware through feedback on Britney Spears’ Instagram pictures and utilizing backdoor Trojans utilizing its personal API.
Turla additionally exploited the hijacked infrastructure and malware of Iranian Apt Oilrig to mislead, deceive, and mislead the defenders and mislead the assaults on Iranian nationwide hackers.
It has just lately been found to hijack the infrastructure of Pakistani menace actor Storm-0156 to focus on Ukrainian army gear linked through Starlink.


