CTM360 has found a brand new international malware marketing campaign referred to as “Clicktok.” This spreads Sparkkitty Spyware and adware to faux Tiktok retailers, steals cryptocurrency wallets and drains funds.
The distinctive, distinctive spy ware Trojan found by the CTM360 is specifically designed to use Tiktok store customers world wide.
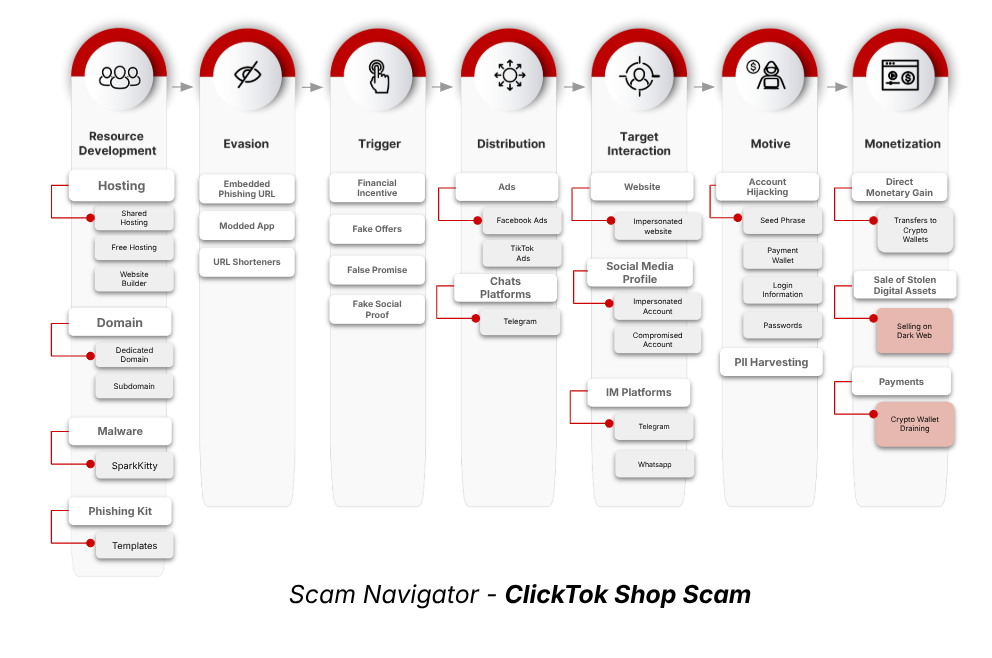
This extremely tuned fraud operation, referred to as “Clicktok,” employs a hybrid fraud mannequin that mixes phishing and malware, deceives patrons and associates program contributors on Tiktok’s rising e-commerce platform, and makes use of associates program contributors.
Within the Clicktok marketing campaign, the Tiktok store was recognized as having embedded Sparkkitty Spyware and adware, a variant much like Sparkcat beforehand recognized by Kaspersky.
As soon as put in, it penetrates the consumer’s gadget, accesses the photograph gallery and extracts screenshots that will comprise cryptocurrency pockets credentials. What makes Clicktok distinctive is its use of phishing and malware techniques concurrently, considerably rising its impression and stealth.
The rip-off begins with impersonation of the business ecosystems of Tiktok, such because the Tiktok store, Tiktok wholesale, and Tiktok mall. Menace actors create faux Tiktok web sites that intently mimic the official interface, making customers assume they’re interacting with the actual platform.
Victims are fascinated by logging in and trying to purchase. In the course of the checkout course of, they’re instructed to pay by way of cryptocurrency wallets.
As soon as fee is made, the Trojanized app with Sparkkitty Spyware and adware embeddings will secretly seize delicate information, together with pockets eligibility, by studying screenshots and pictures saved in your gadget and finally permitting the theft of your digital fund.
The motivation behind Clicktok – Hybrid fraud construction
Attackers have two major functions:
Fishing web site:
They incite customers to open faux store URLs distributed by way of meta advertisements, prompting customers to enter their login credentials, fee particulars, or vendor info. All of those are harvested quietly.
CTM360 tracked the distinctive spy ware Trojan, specifically designed to use customers of Tiktok retailers world wide.
This extremely tuned fraud operation, referred to as “Clicktok,” employs a hybrid fraud mannequin that mixes phishing and malware, deceives patrons and associates program contributors on Tiktok’s rising e-commerce platform, and makes use of associates program contributors.
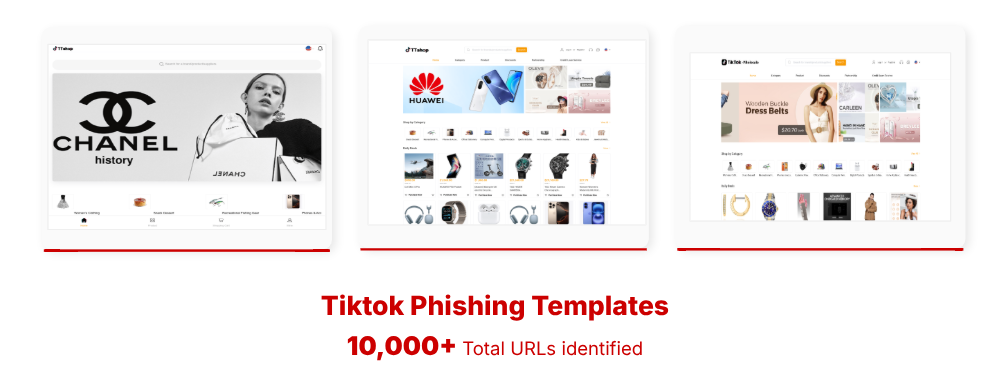
Trojanized Apps:
On cellular, the location encourages customers to put in modified Tiktok apps contaminated with Sparkkitty, a malicious spy ware variant that may deep gadget monitoring, cut back clipboards, and theft of {qualifications}.
These faux apps have an correct consumer interface as the unique Tiktok store, and imagine that victims are quietly sucking delicate information within the background whereas interacting with professional Tiktok apps.
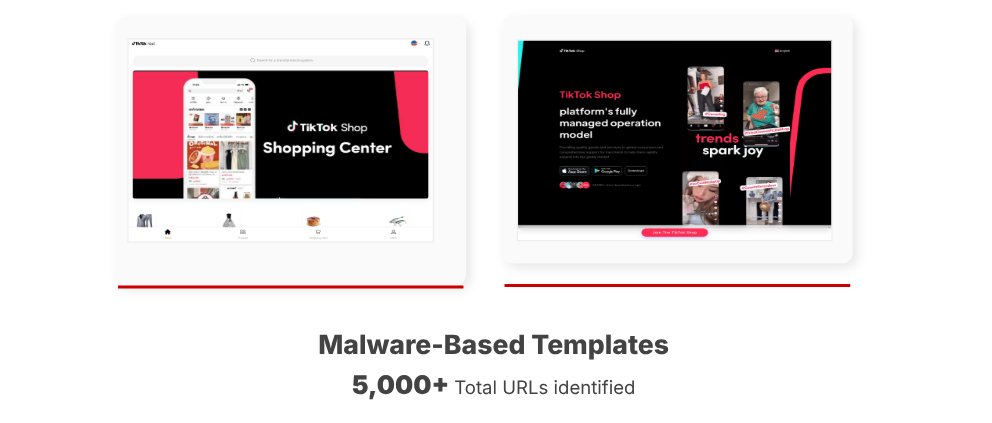
Faux advertisements, AI movies, and domains like look
Clicktok scammers use faux AI-generated movies and meta advertisements to succeed in extra audiences. These advertisements inform customers to forge a fastidiously crafted CyberSquatted area to appear to be an precise Tiktok URL.
Thus far, the CTM360 has noticed:
-
Over 10,000 Tikk web sites use free or cheap TLDs reminiscent of .prime, .store, .icu.
-
Unfold by over 5,000 distinctive malicious app cases, QR codes, messaging apps, and in-app downloads.
A rip-off marketing campaign that impersonates Tikku wholesale and Tikku mall, not simply Tikku store.
Motivation and monetization
The Clicktok marketing campaign makes use of the faux Tiktok store login web page to gather consumer credentials and malware supply by way of the Trojanized app that enables account hijacking. It implements another fee construction that excludes conventional card transactions and requires funds by way of cryptocurrency wallets as a substitute.
Victims are sometimes advisable to “replenish” digital currencies like faux ticock wallets, USDT, ETH, and extra.
CTM360 Suggestions
The CTM360 urges customers and organizations to stay vigilant and take the next precautions:
-
Don’t obtain modified, cracked or unknown software program, particularly from torrent websites or telegrams.
-
All the time examine the area’s reliability and manually examine for spelling errors or suspicious area extensions earlier than coming into your login or fee info.
-
Report any suspicious Tiktok-related content material, advertisements, or apps on to Tiktok or cybersecurity authorities in your nation.
-
Manufacturers and sellers ought to repeatedly monitor model abuse and spoofing tendencies utilizing risk intelligence platforms.
-
A robust anti-virus or EDR answer to stop Sparkkitty spy ware violations.
-
In case you are utilizing a crypto pockets, use a pockets that’s protected by the clipboard.
Learn the entire Clicktok Sparkkitty report.
CTM360 has carried out a deep evaluation of Clicktok scams and revealed an in depth report on Clicktok Trojan.
Learn the entire Clicktok report
Detect 24/7 cyber threats with CTM360
Monitor, analyze and quickly mitigate danger throughout your exterior digital panorama with the CTM360.
Be part of the Group Version
Sponsored and written by CTM360.



