Over 1,000 CrushFTP cases at present revealed on-line are weak to hijacking assaults that make the most of important safety bugs and supply administrator entry to the online interface.
Safety vulnerabilities (CVE-2025-54309) mistreat AS2 validation and have an effect on all CrushFTP variations beneath 10.8.5 and 11.3.4_23. The seller tagged the flaw as actively exploiting an aggressively exploited assault on Wild on July nineteenth. That is one thing we now have but to search out proof to substantiate this.
“There is a 0-day exploit that may be seen within the CST wild on July 18th at 9am. It is most likely going to final a very long time, however I noticed it. The hackers clearly reverse-engineered the code and located some bugs they’ve already mounted.”
“They’re making the most of it for individuals who aren’t maintaining updated with newer variations. As all the time, we advocate patching them commonly and often.
Nevertheless, final week, CrushFTP added that servers saved updated usually are not weak to assaults, and that prospects utilizing unarmed zone (DMZ) cases to isolate their primary servers usually are not affected by the vulnerability.
The corporate additionally recommends importing and downloading logs for extraordinary exercise, enabling automated updates, and enabling whitelist IP for server and admin entry.
In response to a scan of the safety risk surveillance platform Shadowserver, roughly 1,040 CrushFTP cases stay in any respect towards CVE-2025-54309, making them weak to assaults.
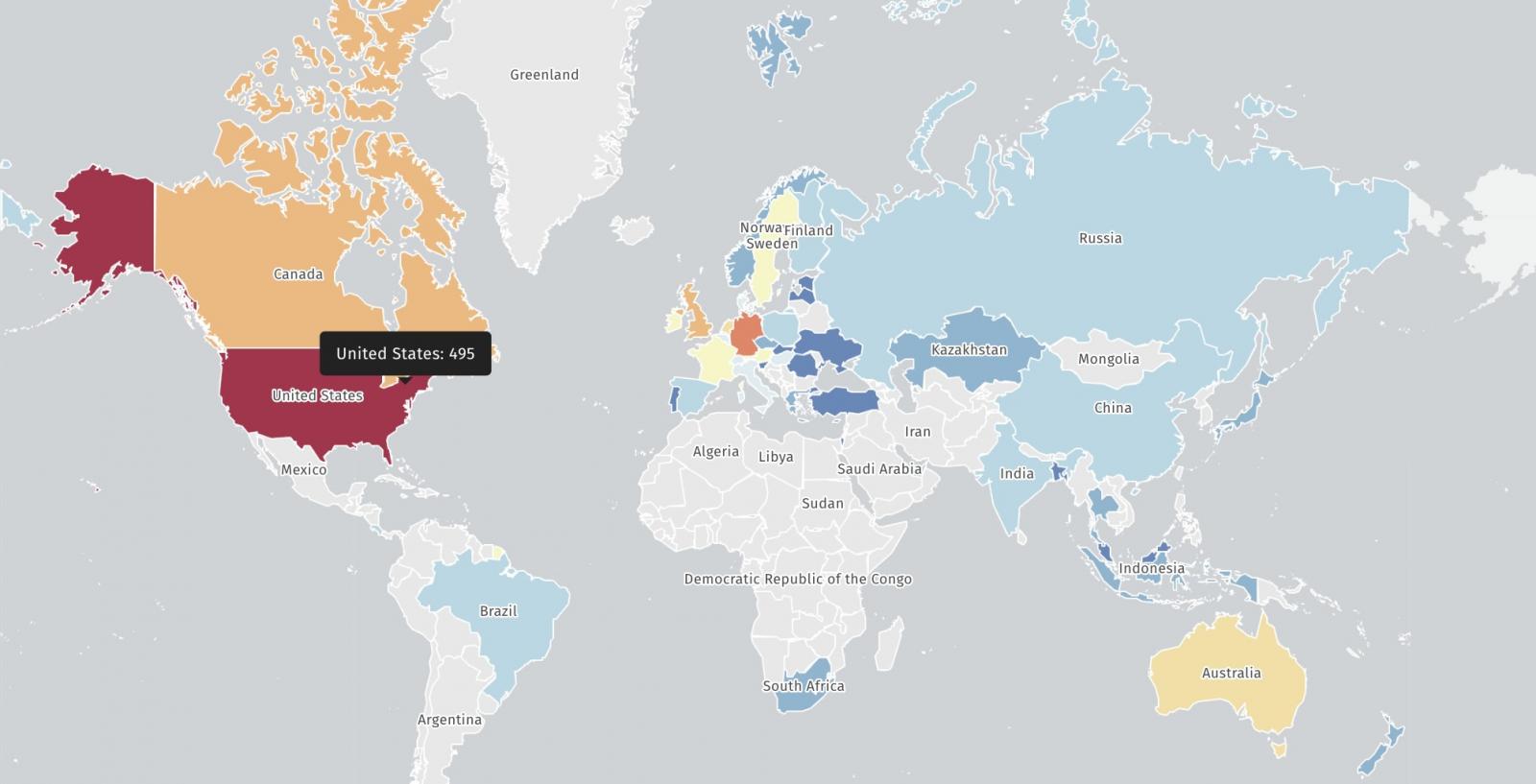
ShadowsServer notifies CrushFTP prospects that their server will not be protected towards ongoing abuse of CVE-2025-54309 and notifies them that they’re exposing their content material to tried information theft.
It’s unclear whether or not these ongoing assaults deployed malware or have been used to theft of information, however managed file switch options like CrushFTP have been a worthwhile goal for ransomware gangs in recent times.
For instance, solely the Clop Cybercrime gang It’s linked to a number of information theft campaigns concentrating on zero-day flaws in Accelion FTA. GoAny The place MFT, MoveIT Switch, and extra just lately CLEO Software program.
A 12 months in the past, in April 2024, CrushFTP was tracked as an aggressively exploited zero-day (CVE-2024-4040))) This allowed an unrecognized attacker to flee from the person’s digital file system (VFS) and obtain the system information.
On the time, cybersecurity firm Crowdstrike focused CrushFTP cases in a number of US organizations and located proof that assaults targeted on intelligence newsletters have been doubtless politically motivated.


